Detection Engineering Lense: Crafting Detections on Threat Actor movement
High-level Overview: This is a continuation of my previous write-up, pivoting from early stage initial access to tracking threat actor (TA) movement within the environment. Given the narrative laid out in the first post, I’ll cut to the chase and dive in to behavior and detection opportunities.
Patient Zero (beachhead_0) Recap
The TA got the party started through a FakeUpdates campaign, where they ran two stages of Javascript and performed a process injection into two separate binaries.
They established their foothold further via persistence (proxy clients written in Python), while they attempted to harvest credentials from a number of sources.
The first source was an attempt to gather login data from the user’s browser session.
powershell -c dir "$env:APPDATA\Mozilla\Firefox\Profiles\*logins.json"
copy "C:\Users\username\AppData\Local\Microsoft\Edge\User Data\Default\Login Data" C:\Users\username\AppData\Local\0395edg.bin&
copy "C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Login Data" C:\Users\username\AppData\Local\0396chr.binThe secondary attempt detonating an encoded powershell block with embedded C# code that implemented the Internal Monologue attack, which is a technique used to extract NTLM hashes or credentials of the currently logged-in user without making external network connections.
The third attempt was the email signature injection that was explained in the first segment.
You don’t have to go home, but you can’t stay here
To get us back on track, the TA has credentials and an established foothold. Now they have to move towards their actions-on-objective.
Wsmprovhost.exe is the Windows Remote Management (WinRM) host process. It’s the executable that runs on a target system to handle incoming WinRM sessions. Threat actors abuse this process to execute commands or payloads remotely, making it a tool of choice for lateral movement.
Note: WinRM is the transport and protocol (client-to-target communication). wsmprovhost.exe is the execution engine on the target—where the rubber meets the road.
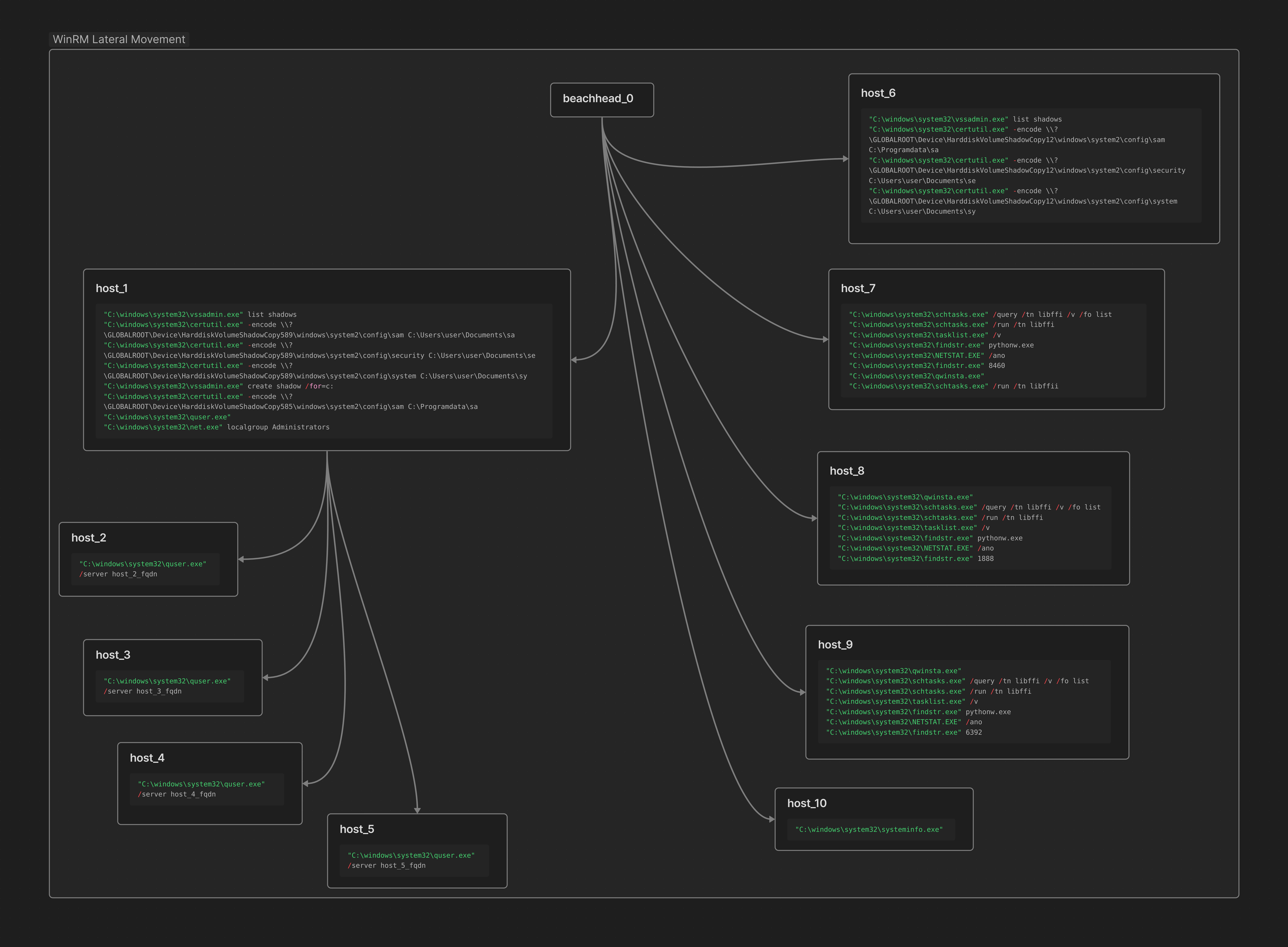
The TA, through the injected process RtkAudUService64.exe, authenticates to a target system over WinRM (ports 5985/HTTP or 5986/HTTPS). Following a successful authentication, wsmprovhost.exe spawns on the target, hosting the session and executing commands sent from the source.
In our story, the commands issued over WinRm targeted task execution, session enumeration, and credential dumping.
wsmprovhost.exe spawns a variety of living-off-the-land binaries (LOLbins)
"C:\windows\system32\quser.exe" /server <FQDN>- Queries user sessions on a specific remote host —discovery (T1033) and lateral movement reconnaissance (T1021) to identify active users.
"C:\windows\system32\qwinsta.exe"- Queries active user sessions — discovery (T1033) to identify logged-in users or sessions for lateral movement (T1021).
"C:\windows\system32\schtasks.exe" /query /tn libffi /v /fo list- Enumerates details of a scheduled task (
libffi) — used for reconnaissance (T1053.005) to check persistence or scheduled payloads.
- Enumerates details of a scheduled task (
"C:\windows\system32\schtasks.exe" /run /tn libffi- Executes an existing scheduled task (
libffi) — persistence or payload execution (T1053.005), often to run malicious code on demand.
- Executes an existing scheduled task (
"C:\windows\system32\tasklist.exe" /v- Lists running processes with verbose details — discovery (T1057) to identify targets, security software, or processes for injection.
"C:\windows\system32\findstr.exe" pythonw.exe- Searches process output (e.g., from
tasklist) forpythonw.exe— discovery (T1057) to locate specific processes for targeting.
- Searches process output (e.g., from
"C:\windows\system32\netstat.exe" /ano- Displays network connections with process IDs — network discovery (T1046) to map connectivity and identify open ports.
"C:\windows\system32\findstr.exe" 8460- Filters network output (e.g., from
netstat) for a specific process identifier (PID) — discovery (T1057) to pinpoint a process’s network activity.
- Filters network output (e.g., from
"C:\windows\system32\systeminfo.exe"- Gathers detailed system configuration data — discovery (T1082) to profile the target system.
Mapping via Canvas - WinRM Movement
Hunting / Detection Opportunities
Detection 1: Scheduled Tasks via WinRM
Back to one of my favorite topics - persistence. This rule doesn’t fall far from the tree of the previous article highlighting scheduled task creation. Upon further review of the incident data, I found that while the original detection caught the majority of the scheduled tasks, there was still opportunity for improvement.
The original query required command-line parameters to sift through the noise, however we can target the use of schtasks directly from wsmprovhost.exe with relative ease.
title: Remote Scheduled Task Creation via WinRM or Unverified Parents
id: 789ef012-34gh-56ij-78kl-901234567890
description: Detects process creation events on Windows where an unverified or WinRM-related parent process spawns a child process with command-line arguments indicating remote scheduled task creation.
status: stable
author: bencrypted
date: 2025/02/27
logsource:
category: process_creation
product: windows
detection:
parent_filter:
# Parent process conditions: unverified signature or specific WinRM-related names/display names
ParentCodeSignature|notin:
- 'valid'
- 'verified'
ParentImage|endswith|all:
- '\wsmprovhost.exe'
- '\winrshost.exe'
ParentOriginalFileName|endswith:
- 'Host process for WinRM plug-ins'
- "Host Process for WinRM's Remote Shell plugin"
parent_exclusion:
ParentImage|endswith:
- '\msiexec.exe'
- '\svchost.exe'
remote_schtasks:
Image|endswith: '\schtasks.exe'
CommandLine|contains|all:
- ['create', 'run', 'query']
condition: (parent_filter and not parent_exclusion) and remote_schtasks
fields:
- ParentImage
- Image
- CommandLine
- ParentCodeSignature
- ParentOriginalFileName
falsepositives:
- Legitimate administrative use of WinRM to create scheduled tasks
level: highDetection 2: Shadow Copy Access
I was able to hone in on a wide array of parent processes with no false positives across historical data. Detections like these are a huge win as they are difficult to evade, and the likelihood that a TA will trip this alarm is high.
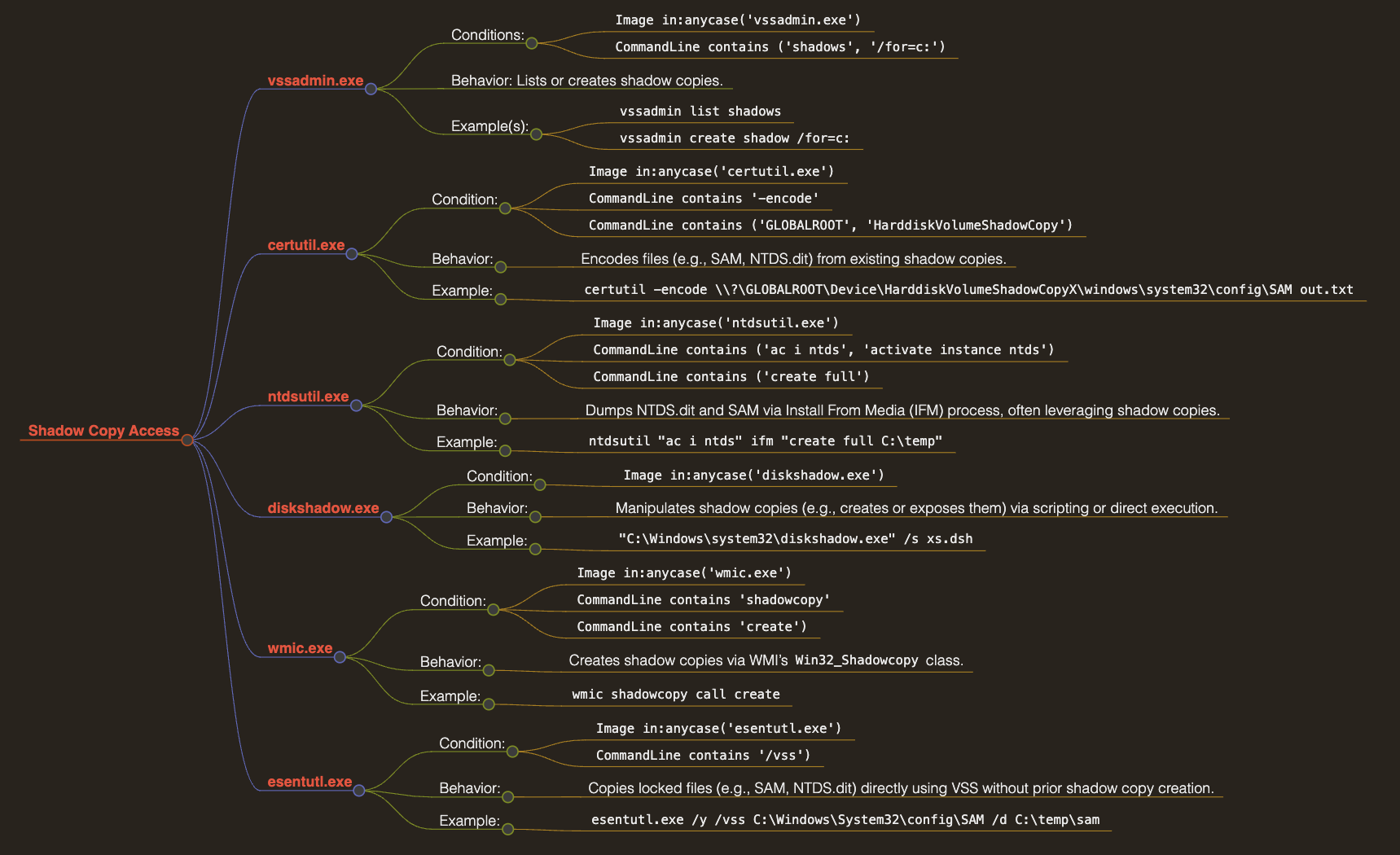
While this covers a large array of behavior, there are a few methods that could still bypass this rule. A process like OneDriveStandaloneUpdater.exe, if injected with malicious code, can directly execute another executable such as ntdsutil.exe or vssadmin.exe without necessarily invoking a command-line interpreter like cmd.exe or powershell.exe. This is more on the rare side with templated attacks, however it is not impossible.
title: Shadow Copy Access (edr-cred-proc-shadow-copy-abuse)
id: 789fcdeb-34c5-4d78-91bc-426614174003
description: "Identifies LOLbin parents spawning tools to manipulate Volume Shadow Copies for credential dumping (MITRE: T1003.002, T1003.003, T1047, T1218, T1490)"
status: experimental
author: bencrypted
date: 2025/01/20
logsource:
category: process_creation
product: windows
detection:
selection_parent:
Image|endswith:
- '\cmd.exe'
- '\wscript.exe'
- '\cscript.exe'
- '\rundll32.exe'
- '\regsvr32.exe'
- '\wmic.exe'
- '\mshta.exe'
- '\powershell.exe'
- '\pwsh.exe'
- '\powershell_ise.exe'
- '\wmiprvse.exe'
- '\wsmprovhost.exe'
- '\winrshost.exe'
selection_vssadmin:
Image|endswith: '\vssadmin.exe'
CommandLine|contains: 'delete shadows'
selection_certutil:
Image|endswith: '\certutil.exe'
CommandLine|contains: '-encode'
selection_ntdsutil:
Image|endswith: '\ntdsutil.exe'
CommandLine|contains: 'ifm'
selection_diskshadow:
Image|endswith: '\diskshadow.exe'
CommandLine|contains: 'list shadows'
selection_wmic:
Image|endswith: '\wmic.exe'
CommandLine|contains: 'shadowcopy create'
selection_esentutl:
Image|endswith: '\esentutl.exe'
CommandLine|contains: '/vss'
filter_parent:
CommandLine|contains: 'tss.ps1'
condition: selection_parent and (selection_vssadmin or selection_certutil or selection_ntdsutil or selection_diskshadow or selection_wmic or selection_esentutl) and not filter_parent
fields:
- Image
- CommandLine
- ParentImage
falsepositives:
- Legitimate administrative tasks
level: high
tags:
- attack.credential_access
- attack.execution
- attack.defense_evasion
- attack.t1003.002
- attack.t1003.003
- attack.t1047
- attack.t1218
- attack.t1490Detection 3: User-context across multiple endpoints
This is one of those simple ideas that is difficult in practice. This could perhaps reach the limits of your existing detection capabilities, depending on your rule stack and logging.
title: Clustered Suspicious Process Creation Across Multiple Hosts
id: 456cd789-12ef-34gh-56ij-789012345678
description: Detects clustered process creation events on Windows within a 30-minute interval for a single user across 2-3 distinct hosts, where unverified or WinRM-related parent processes spawn children with command-line arguments suggesting reconnaissance, persistence, or malicious activity.
status: experimental
author: bencrypted
date: 2025/02/27
logsource:
category: process_creation
product: windows
detection:
parent_filter:
# Parent process conditions: unverified signature or specific WinRM-related names/display names
ParentCodeSignature|notin:
- 'valid'
- 'verified'
ParentImage|endswith|all:
- '\wsmprovhost.exe'
- '\winrshost.exe'
ParentOriginalFileName|endswith:
- 'Host process for WinRM plug-ins'
- "Host Process for WinRM's Remote Shell plugin"
parent_exclusion:
ParentImage|endswith:
- '\msiexec.exe'
- '\svchost.exe'
suspicious_cmdline:
CommandLine|contains:
- 'schtasks'
- 'qwinsta'
- 'tasklist'
- 'certutil'
- 'vssadmin'
clustering:
timeframe: '30m'
group_by:
- 'User'
- 'Host'
event_threshold: 3
host_threshold: 2
condition: (parent_filter and not parent_exclusion) and suspicious_cmdline | count > clustering.event_threshold by clustering.group_by within clustering.timeframe and distinct(Host) >= clustering.host_threshold
fields:
- ParentImage
- Image
- CommandLine
- ParentCodeSignature
- ParentOriginalFileName
- User
- Host
falsepositives:
- Legitimate administrative scripts executed via WinRM or unverified tools across multiple hosts in a short interval
level: critical